Filter Port-Specific Traffic
Scenario Description
As shown in the figure, the R&D department uses Router A to access the Internet, and it provides WWW services for the branch office at 202.120.1.139. ACL Management connects to Router A through 88.1.10.1. External attackers use UDP port 4444 to initiate virus attacks.
For information security, the company wants to deploy ACLs to:
- Discard external attack packets from UDP port 444.
- Allow the packets from only the brand office to the WWW Server through port 8080.
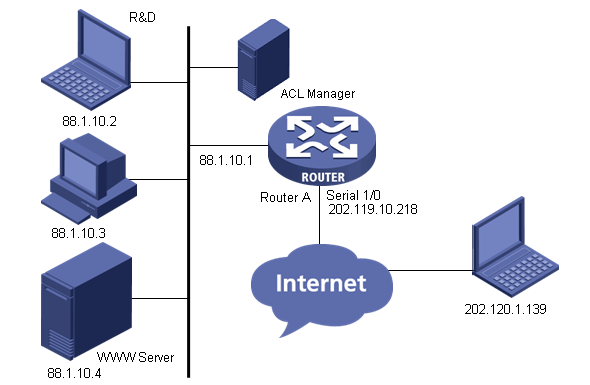
Network diagram
Scenario Analysis
Deploy an ACL to Serial 1/0. In the ACL, configure the following rules:
- To discard external attack packets from UDP port 444, configure a rule to deny incoming traffic with destination UDP port 4444.
- To allow the packets from only the brand office to the WWW Server through port 8080, configure a rule to permit TCP packets. The source IP address of the TCP packets is 202.120.1.139, the destination IP address is 88.1.10.4, and destination port is 8080.
Operation Procedure
- Add device to the the system platform.
In the the system platform homepage, click Add Device in the My Shortcut tree. Type 88.1.10.1 (IP address of Router A) in the Host Name/IP text box, and click OK.
- Add ACL resource.
a. Select the Service tab, select ACL Management and click ACL Resource in the navigation tree, click Add and then click Common ACL Resource to enter the ACL Resource page.
b. Select Advanced for ACL Type, type the ACL identifier 3001 and enter the ACL resource name Control Port Access, then click OK.
- Add ACL rule set.
a. In the ACL Resource page, click the 3001 identifier link.
b. Click Add. Enter the basic information and click Next.
c. Click Add. Set the protocol to udp, set the action to deny, set the time range to Undefined, select Specified Port in the Destination Port area, select Equal and type 4444, accept the defaults for the other items, and finally click OK.
d. Click Add to enter the Add Rule page. Set the protocol to tcp, set the action to permit, set the time range to Undefined, select IP Address/Mask in the Source Address area and type 202.119.1.139/32, select IP Address/Mask in the Destination Address area and type 88.1.10.4/32, select Specified Port in the Destination Port area, select Equal and type 8080, accept the defaults for the other items, and finally click OK.
e. Click Add to enter the Add Rule page. Set the protocol to ip, set the action to deny, set the time range to Undefined, select All in the Source Address area, input 88.1.10.4/32 in the Destination Address area, accept the defaults for the other items, and finally click OK.
f. Click Finish.
- Access ACL Devices.
a. Select the Service tab, select ACL Management and click ACL Devices in the navigation tree to show the ACL device list. Click the ACL Config link  of Router A to enter the ACL configuration page of Router A.
of Router A to enter the ACL configuration page of Router A.
- Add ACL definition.
a. Select the ACL Definitions tab and click Add. Select 3001 and the rule set you have just added, and then click Next.
b. Click Deploy. Set the task name to setRule5, set the deployment order to Serial, set the error handling mechanism to Stop all deployments when error occurs, set the execution time to Immediately, and then click OK.
- Add ACL use.
a. Select the ACL Uses tab and click Add. Set the service type to Packet Filter, and then click Next.
b. Set the filter direction to inbound, select Serial 1/0, and then click Next.
c. Select 3006 and click OK.
d. Set the task name to addApp5, set the deployment order to Serial, set the error handling mechanism to Stop all deployments when error occurs, set the execution time to Immediately, and then click OK.
Precautions
- IP address masks are used in ACL Management, and inverse masks are used on devices.
- After the deployment, you can view the result in the task list. Only Succeeded indicates the deployment is successful.