Deploy ACLs in Bulk for Access Control
Scenario Description
As shown in the following figure, an S8500 connects the campus network to the Internet. Several S6500 switches run on the convergence layer, which cooperate with a series of S3900 switches to form the access layer for authentication and access control. The 16 S3900 switches with their IP addresses ranging from 10.10.112.21 to 10.10.112.36 are on the access layer.
The network center wants to deploy ACLs on the access layer through ACL Management to deny the access to external IP address 202.118.19.88.
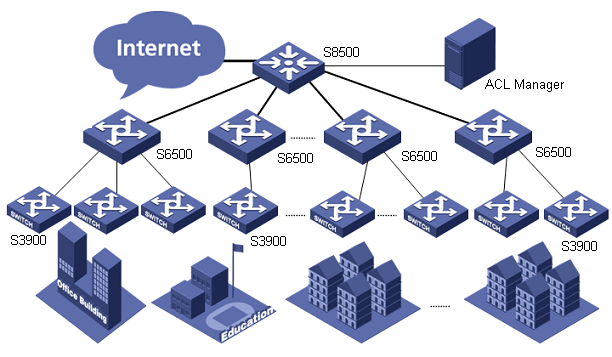
Network diagram
Scenario Analysis
To deny the campus users to access the IP address 202.118.19.88, deploy ACLs to all Ethernet interfaces of S3900 switches to discard packets destined to 202.118.19.88.
Operation Procedure
- Add device to the the system platform.
In the the system platform homepage, click Add Device in the My Shortcut tree. Type the IP addresses (from 10.10.112.21 to 10.10.112.36) of all the S3900s to be managed in the Host Name/IP text box.
- Add ACL template.
a. Select the Service tab, select ACL Management and click ACL Template in the navigation tree, and then click Add.
b. Set the template name to batchACLCfg, the type to Advanced and the description to Batch ACL configuration.
c. Click Add Rule to enter the Add Rule page. Set the protocol to ip, set the action to deny, left the time range blank, select All in the Source Address area, select IP Address/Mask in the Destination Address area and type 202.118.19.88/32, accept the defaults for the other items, and finally click OK.
d. Click OK.
- Add ACL resource.
a. Select the Service tab, select ACL Management and click ACL Resource in the navigation tree, click Add and then click Common ACL Resource to enter the ACL Resource page.
b. Select Advanced for ACL Type, type the ACL identifier 3039 and enter the ACL resource name Batch Deploy, then click OK.
- Add ACL rule set.
a. In the ACL Resource page, click the 3039 identifier link.
b. Click Import from Template, select batchACLCfg, and then click Next.
c. Enter the basic information of the rule set.
d. Keep Configure ACL Rules with Time Range unselected and click Next.
e. Click Finish without selecting any rule.
- Deploy ACL.
a. Select the Service tab, select ACL Management and click ACL Deployment in the navigation tree, and then click the Deploy ACLs link.
b. Select all the devices with their IP addresses ranging from 10.10.112.21 to 10.10.112.36, select ACL resource 3039, and then click Next.
c. Click Deploy. Set the task name to setRule3, set the deployment order to Serial, set the error handling mechanism to Stop all deployments when error occurs, set the execution time to Immediately, and finally click Next.
d. Click OK.
- Deploy ACL use.
a. Select the Service tab, select ACL Management and click ACL Deployment in the navigation tree, and then click the Deploy ACL Uses link.
b. Select Packet Filter and click Next.
c. Select all the devices with their IP addresses ranging from 10.10.112.21 to 10.10.112.36, and click Next.
d. Set the filter direction to inbound, select all ports and same choice for other devices, and then click Next.
e. Type 3039 and click Next.
f. Click OK.
g. Set the task name to addApp3, set the deployment order to Serial, set the error handling mechanism to Stop all deployments when error occurs, set the execution time to Immediately, and then click OK.
Precautions
- If you set the port number, time range or IP address as a variable when adding a template, you are required to add or select the variables after basic information setting in the operation of adding ACLs in batches. Variables are not used in this example, so this step is skipped.
- In deploying an ACL use, the Same choice for other devices is not selected when selecting devices, you need to select interfaces for each device. If this option is selected, inexistent interfaces are automatically filtered.
- IP address masks are used in ACL Management, and inverse masks are used on devices.
- After the deployment, you can view the result in the task list. Only Succeeded indicates the deployment is successful.
