Third-Party Authentication
This function authenticates third-party users. An authenticated third-party user is assigned a user account to log into INC. Information about third-party users can be updated manually by the operator or automatically synchronized from the third-party server to INC.
Operation Procedure
- Click the User tab.
- From the navigation tree, select User Access Policy > Third-Party Authentication.
- Click
 . The page for configuring third-party authentication appears.
. The page for configuring third-party authentication appears.
Parameters
- Enable Third-Party Authentication: Before you enable third-party authentication, make sure no on-demand LDAP synchronization policy exists. Otherwise, you cannot configure a third-party authentication.
- Authentication Method
- Third-Party Authentication First: To authenticate a third-party user, INC first searches the third-party database. If the third-party database cannot be connected, INC uses the local database.
- Local Authentication First: To authenticate a third-party user, INC first searches the local database. If no match is found, INC uses the third-party database.
-
Third-Party Database
- Basic Information
- The Basic Information area includes Database User Name, Database Password, Database Server IP, Database Name, and Database Server Port.
- When a SQL server database is used, the default value of Database Server Port is 1433. You can modify the port as needed. You must also specify Database Instance for the SQL server database. When another type of database is used, you do not need to specify this parameter.
- When a MySQL database is used, the default value of Database Server Port is 3306. You can modify the port as needed. You must also specify Database Character Set for the MySQL database.
- When an Oracle database is used, the default value of Database Server Port is 1521. You can modify the port as needed. you must specify Database Service Name and User Identity.
- When a PostgreSQL database is used, the default value of Database Server Port is 5432. You can modify the port as needed.
- Click Test Connectivity to test whether the INC system can be correctly connected to the database.
- Collaboration Policy
- User Group: By default, User Group is set to Ungrouped. You can also select another user group as needed.
- Password Encryption Type: The options are Plaintext, DES, 3DES, IDEA, RC5, MD5,and Custom. You can select Encode the encryption result with Base64 for all password encryption types except the MD5andCustom options.
- If you select DES, 3DES, IDEA, or RC5 from the Password Encryption Type list, you must specify a value in the Encryption Key field. For DES, the encryption key must be eight-digit. If you select Custom from the Password Encryption Type list, you must import a custom password plugin.
- Import Password Plugin:You can write and import a plugin for password encryption and decryption if passwords are encrypted on the server. Write a .dll file for Windows or a .so file for Linux. Before you write the plugin, first download the correct header file based on the bit version of the JDK on the OS. Use the following guidelines to generate the .dll or .so file:
1. Select the JDK of the same bit version as the JDK installed on the INC server.
2. Make sure the version of the selected JDK is not higher than the version of the JDK installed on the INC server.
3. In Linux, use the GNU C++ compiler.
- When Authentication Method is set to Third-Party Authentication First, the Authentication SQL parameter is required. When Authentication Method is set to Local Authentication First, the Authentication SQL parameter is optional.
- Authentication SQL: Its value is in the format of SELECT [Password Field] FROM [Table/View Name] WHERE [Username Field] = ?. If you need to specify the end time for the user, the value is in the format of SELECT [Password Field] [End time] FROM [Table/View Name] WHERE [Username Field] = ?. Authentication SQL can include multiple query criteria. You can add query criteria to the authentication SQL.
- Support Backup:
1. Select this option as needed. When you select this option, you must configure backup settings.
2. Delete Local User: Deletes the user from the local database if the user does not exist in the third-party database. This parameter appears when the CAMS component is not installed.
3. Create Local Accounts for Third-Party Users: Select this parameter to synchronize qualified accounts to EIA to create local accounts according to the backup SQL database.
4. Locally Encrypt and Back up User Passwords: Select this parameter to enable EIA to encrypt and store the password of an account through the INC encryption method when creating the account locally.
5. Backup SQL: Click Edit. Enter a SQL statement in the dialog box and click OK. INC automatically checks for SQL statement incorrectness. The fields that meet the requirements appear. Select fields as needed. Use the alias if you query data in multiple lists that have the same fields. For example, if both list A and list B have the ID field, the SQL statement is SELECT a.ID AS AID, b.ID AS BID FROM A a, B b.
6. Backup Interval: Specifies the days at which INC backs up the third-party database at the specified hour. The Days value is an integer in the range of 1 to 365. The Hour value is an integer in the range of 0 to 23.
7. Select at least the following backup fields: User Name, ID Number, Account Name, and Password.
8. Set the following parameters as needed: Telephone, Contact Address, E-mail, Account Type, Prepaid Money, Self-Service Recharge, End time, Max. Idle Time, Max. Concurrent Logins, Max. Smart Device Bindings for Portal, Login Message, Device IP, Port, VLAN ID, Outer VLAN ID, User SSID, and Device SN. Account Type, Prepaid Money, and Self-Service Recharge appear when the CAMS component is installed.
9. If a user already exists in the INC system, to update a parameter value, you must select a value from the list, instead of manually entering a value.
- Access Information
- Max. Concurrent Logins: Maximum number of concurrent online users of the same account, in the range of 1 to 255. If this field is empty, the number of concurrent online users of the account is unlimited.
- Access Service
- Select one or more access services from INC. If you select multiple services, make sure the selected services have different service suffixes.
- Mobile Office Service
- Allows you to use the mobile office function to define scenario-based mobile application policies, mobile endpoint configuration policies, mobile endpoint compliance policies, secure mailbox policies, VPN control policies, and secure desktop policies. This parameter is available when the EMO component is installed.
- Check Configuration
- After completing configuration settings, use Test Username and Test Password to test the configuration.
-
Third-Party Web Service
- Basic Information
- This function provides a third-party Web service interface to authenticate third-party users. The Basic Information area includes Web Interface Method, Request Mode, Identity Check Mode, Web Service URL, and Password Encryption Type.
- Web Interface Method: When the HTTP/HTTPS option is used, the system sends authentication requests to the specified third-party service URL by using the specified username, password, endpoint IP address and endpoint MAC address. When the REST option is used, the system sends authentication requests to the specified third-party service URL. The URL must include the fields ${username} and ${password} to indicate the username and the password. The third-party system authenticates the user based on the combination of the user name and the password. When the POST option is used, you must specify XML Message Body. The XML message body must include the fields ${username} and ${password}.The URL include the fields ${mac} and ${ip} to indicate the endpoint MAC address and the endpoint IP address.
- String before Password/String after Password: When Use the password returned by the Web interface is selected from the Identity Check Mode list, you must specify these two fields to obtain user's password for authentication. If you do not specify these two fields, all characters returned by the Web interface are treated as the password.
- Request Head: Enter a parameter string in each line, including the name and value separated by colon. For example, Pragma:no-cache. You can enter a maximum of 20 lines.
- Add Users by Third Party: Select this option to allow the third-party system to add access users to UAM. This option is available only when Access Web Interface for Authentication is used as the identity check mode. If you select this option, the third-party system must first use the INC RESTful interface to create accounts for users before they are authenticated by EIA. If you do not select this option, EIA first determines whether a third-party account exists in the INC system before authenticating this account. If this account does not exist in the INC system, EIA first creates the account and then performs account authentication.
- The operator must login to use the Web interface: When you select this option, you must specify Operator and Password.
When you select Use Proxy Server, you must specify the IP address or domain name and port number of the proxy server.
- User Group: By default, User Group is set to Ungrouped. You can also select another user group as needed.
- Authentication Success Identifier: The authentication process is considered to be successful only when the returned value set includes this identifier.
- String Before Failure Message/String After Failure Message: The authentication succeeds only if the authentication response contains the authentication success identifier. For an authentication failure response, the system takes the content between the specified strings before and after the failure message as the failure message. When no such strings are specified, the system takes the entire response as the failure message. For example, when the authentication success identifier is success and the response is "{"code":"E255","msg":"wrong username or password","data":null}", the authentication is considered failed. After you specify the strings before and after the failure message as "msg":" and ","data", the system takes wrong username or password as the failure message. Upon authentication failures, the system generates authentication failure logs, which do not contain the failure messages.
- Password Encryption Type: The options are Plaintext, DES, 3DES, IDEA, RC5, MD5, and Custom. You can select Encode the encryption result with Base64 for all password encryption types except the MD5andCustom options. If you select DES, 3DES, IDEA, or RC5 from the Password Encryption Type list, you must specify a value in the Encryption Key field. For DES, the encryption key must be eight-digit. If you select Custom from the Password Encryption Type list, you must import a custom password plugin.
- Import Password Plugin:You can write and import a plugin for password encryption and decryption if passwords are encrypted on the server. Write a .dll file for Windows or a .so file for Linux. Before you write the plugin, first download the correct header file based on the bit version of the JDK on the OS. Use the following guidelines to generate the .dll or .so file:
1. Select the JDK of the same bit version as the JDK installed on the INC server.
2. Make sure the version of the selected JDK is not higher than the version of the JDK installed on the INC server.
3. In Linux, use the GNU C++ compiler.
- Access Information
- Max. Concurrent Logins: Maximum number of concurrent online users of the same account, in the range of 1 to 255. If this field is empty, the number of concurrent online users of the account is unlimited.
- Access Service
- Select one or more access services from INC. If you select multiple services, make sure the selected services have different service suffixes.
- Check Configuration
- After completing configuration settings, use Test Username and Test Password to test the configuration.
-
Customize Third-Party Plugin
- Basic Information
- Identity Check Mode: This option enables UAM to function as a third-party plugin. UAM provides an authentication interface and interacts with the third-party database to authenticate users. The process is as follows:
Method 1:
(1) Implement the plugin authentication and authentication method defined in the ThirdPartPluginMgr interface.Configure authenticate(String username, StringBuilder password). The password is also used as the carrier for the returned password.
(2) Use the text editor to open the <INC installation path>/uamthirdpartyauth/conf/acmAuthNPluginCfg.xml file. Replace ThirdPartPluginMgrImpl with the complete implementation class path.
(3) After the implementation class is compiled into a class file, a jar package is generated and stored in <INC installation path>/uamthirdpartyauth/repository. Reboot the uamThirdAuth process on UAM.
Method 2 (recommended for EIA E0510 and later):
(1) Implement the plugin authentication and authentication method defined in the ThirdPartPluginExtensionMgr interface.Configure authenticate(StringBuilder params). Input the StringBuilder params parameter in the following format with each field separated by using \n: username\npassword\nIP address\nMAC address. For example, zhangshan\n123456\n1.1.1.1\n11:11:11:11:11:11.
(2) Use the text editor to open the uamthirdpartyauth/conf/acmAuthNPluginCfg.xml file in the <INC installation path>. Replace ThirdPartPluginMgr with ThirdPartPluginExtensionMgr.
(3) Use the text editor to open the uamthirdpartyauth/conf/acmAuthNPluginCfg.xml file in the <INC installation path>. Replace ThirdPartPluginMgrImpl with the complete implementation class path.
(4) After the implementation class is compiled into a class file, a jar package is generated and stored in uamthirdpartyauth/repository of the INC installation path. Reboot the uamThirdAuth process on UAM.
(5)If Use the password returned by the Web interface for authentication is selected, set the value of params to the returned password.
- User Group: By default, User Group is set to Ungrouped. You can also select another user group as needed.
- Process Username: Remove or keep the service suffix in usernames according to the third-party authentication requirements.
- Add Users by Third Party: Select this option to allow the third-party system to add access users to UAM. This option is available only when Access Web Interface for Authentication is used as the identity check mode. If you select this option, the third-party system must first use the INC RESTful interface to create accounts for users before they are authenticated by EIA. If you do not select this option, EIA first determines whether a third-party account exists in the INC system before authenticating this account. If this account does not exist in the INC system, EIA first creates the account and then performs account authentication.
- Support Backup: When you select this option, the system periodically synchronizes or deletes authenticated third-party users at the specified intervals.
Implement the processUserData method defined in the authentication interface. The returned user information must meet the requirements of the standard XML format.
- Delete Local User: Deletes the user from the local database if the user does not exist in the third-party database. This parameter appears when the CAMS component is not installed.
- Backup Interval: Specifies the days at which INC backs up the third-party database at the specified hour. The Days value is an integer in the range of 1 to 365. The Hour value is an integer in the range of 0 to 23.
- Access Information
- Max. Concurrent Logins: Maximum number of concurrent online users of the same account, in the range of 1 to 255. If this field is empty, the number of concurrent online users of the account is unlimited.
- Access Service
- Select one or more access services from INC. If you select multiple services, make sure the selected services have different service suffixes.
- Check Configuration
- After completing configuration settings, use Test Username and Test Password to test the configuration.
-
Third-Party RADIUS Authentication
- Basic Information
- IP Address: Specifies an IPv4 or IPv6 address of the third-party RADIUS server.
- Standby Server IP: Specifies an IPv4 or IPv6 address of the third-party RADIUS standby server.When the primary server fails, the authentication will switch to the IP address of the standby server.
- Port: Specifies a port number to which the third-party RADIUS server listens for authentication packets.
- Key: Specifies the key for UAM and the third-party RADIUS server to authenticate each other.
- Local Password: Initial password of the third-party RADIUS users. A user can access the self-service center to change the password.
- Password Check Mode: If Third-Party Password + Local Password is selected, a user must provide both the third-party dynamic password and the local password for authentication. The dynamic password is verified by the third-party system and the local password is verified by UAM. If Third-Party Password is selected, a user only needs to provide the third-party dynamic password for authentication.
- Collaboration Policy
- User Group: By default, User Group is set to Ungrouped. You can also select another user group as needed.
- Access Information
- Max. Concurrent Logins: Maximum number of concurrent online users of the same account, in the range of 1 to 255. If this field is empty, the number of concurrent online users of the account is unlimited.
- Access Service
- Select one or more access services from INC. If you select multiple services for a RADIUS server, make sure the selected services have different service suffixes.
- The selected services for different RADIUS servers cannot have the same suffix. The system selects a RADIUS server for authentication based on the service suffix.
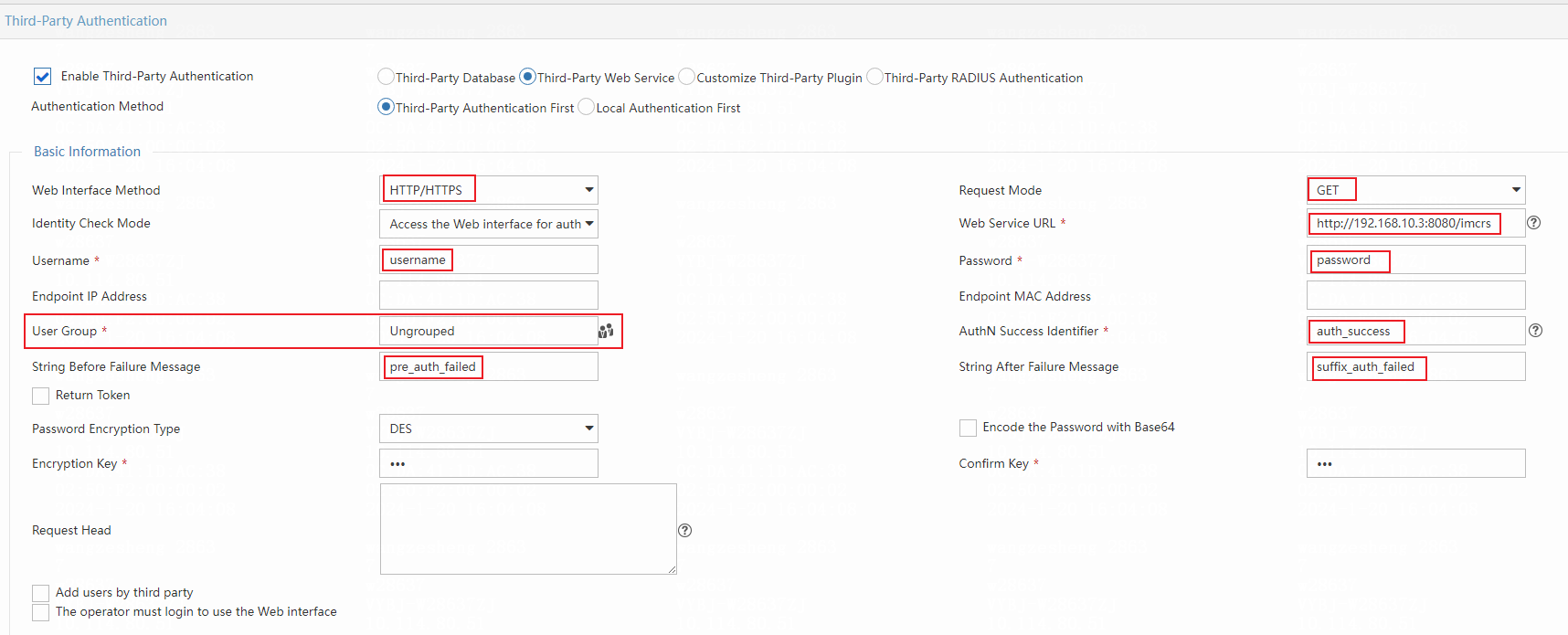
Typical scenarios for configuring the third-party Web service
- Scenario 1:
If the third-party authentication URL is:
Configure third-party authentication as follows:
- Select HTTP/HTTPS for Web Interface Method.
- Select GET for Request Mode.
- Enter http://192.168.10.3:8080 in the Web Service URL field.
- Enter username in the Username field.
- Enter password in the Password field.
- Configure other parameters as shown in the following figure.
In this example, XXX is the authentication account name after URL coding, and *** is the password after DES encryption and URL coding.
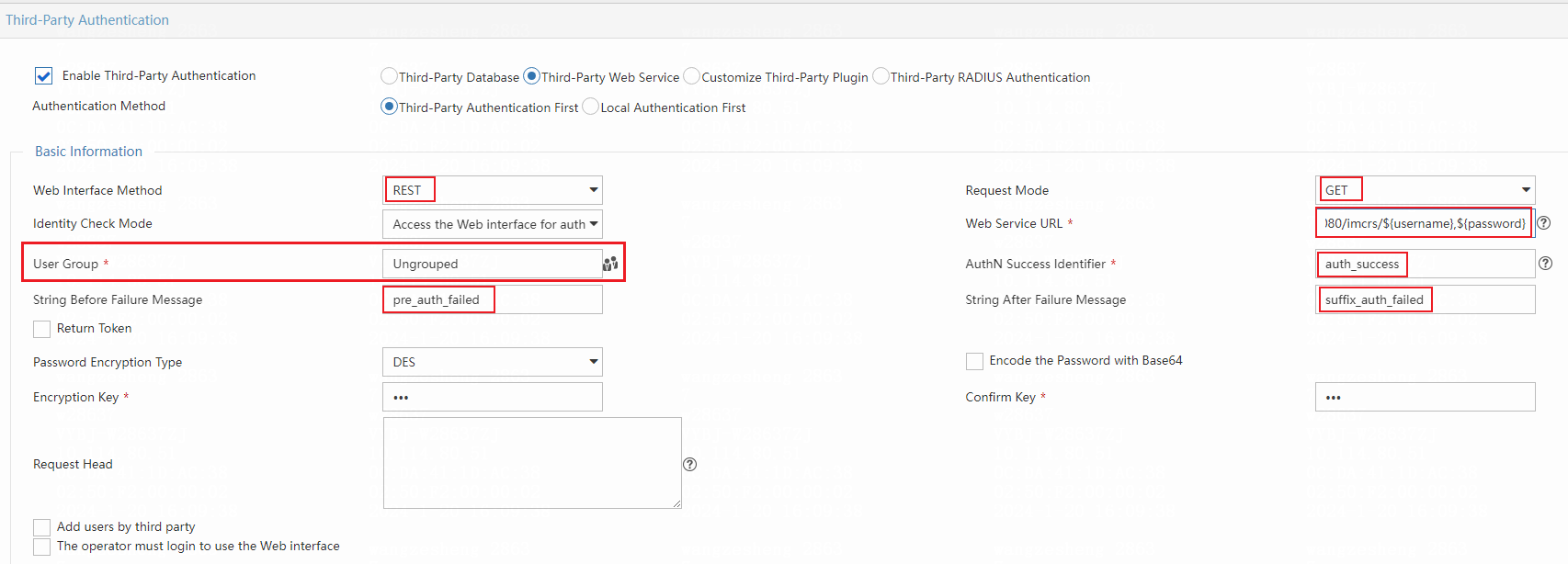
- Scenario 2:
If the third-party authentication URL is:
Configure third-party authentication as follows:
- Select REST for Web Interface Method.
- Select GET for Request Mode.
- Enter http://192.168.10.3:8080 in the Web Service URL field.
- Configure other parameters as shown in the following figure.
In this example, XXX is the authentication account name after URL coding, and *** is the password after DES encryption and URL coding.
Precautions
- The third-party authentication function depends on the uamThirdAuth process.
- For INC to connect to a third-party Oracle database correctly, you must restart the INC server after configuring the environment variables on the INC server.
- For Third-Party Web Service and Customize Third-Party Plugin, if Access the Web Interface for Authentication is selected from the Identity Check Mode list, CHAP, PEAP/MSCHAPv2, and TTLS/MSCHAPv2 are not supported.
- The third-party RADIUS authentication supports the following credential transmission methods: CHAP, PAP, EAP-MD5, PEAP-MD5, and PEAP-GTC. The CHAP method requires the support of the third-party RADIUS server. The EAP-MD5 and PEAP-MD5 methods must work with the iNode client.
- If The third-party RADIUS authentication uses the CHAP authentication method, only the third-party password validation is supported. The third-party password and local password cannot be validated at the same time.
- If The third-party RADIUS authentication uses the CHAP authentication method, the Check Configuration function is not available.
- The third-party authentication does not support device users.
Related Topics

