SCC Help >> SCC Quick Start
SCC Quick Start
SCC Quick Start walks you through the basics of the security control center.
SCC Working Flow
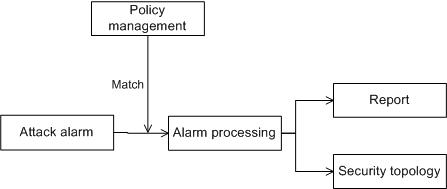
SCC Working Flow Description
The SCC system automatically receives various alarms. If an alarm matches a security control policy defined in the system, the system automatically processes the alarm or you can process the alarm manually. After the processing, a report and topology are generated. With SCC, you need to:
- Define security control policies
- Execute the policies that need to be executed manually
- View the reports and topologies
- Attack alarm: Displays the received attack alarms in the form of a list, and provides basic and advanced query for you to locate the concerned attack alarms.
- Policy management: Security control policies are used to define the association between alarms and actions. An alarm matching a policy triggers the corresponding action defined in the policy, and thus related security measure is used to deal with the alarm. Taking related security measures is one of the alarm processing functions.
- Alarm processing: Alarm processing includes a series of fucntions, such as taking security measures according to the received alarms and taking recovery actions. These functions work together in response to alarms, helping you eliminate network threats. The system provides two interfaces for you to process alarms: realtime alarm monitoring and alarm browsing. Realtime alarm montioring can provide the recent 25/50/75/100/125 alarms, and alarm browsing can provide all the received alarms.
- Report: Reports display the summary information and trends of attack alarms, providing the data for you to analyze the network status.
- Security topology management: Displays detailed information about attack alarms, including the attack paths and the devices connected with the attack sources.

