Device User Authorization Control
Scenario
In a corporation network that has a great number of branches and network devices, to ensure device management security, devices in different areas or of different types need to be managed by different administrators, and the commands that the administrators can execute need to be controlled. TAM can authorize and monitor the administrators, reducing operator workload.
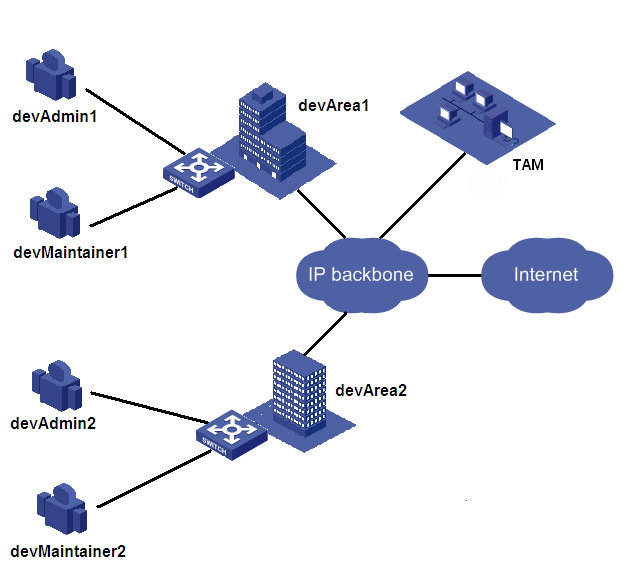
TAM network diagram
Two branches are available: devArea1, and devArea2.
Each branch has one administrator: devAdmin1 and devAdmin2. The administrators have user privilege level 2 and can change their privilege levels to the highest level, and can manage network devices in the branch at any time.
Each branch has one maintainer: devMaintainer1 and devMaintainer2. They have user privilege level 2, and cannot change their privileges to a higher level. They can manage the devices only at office hour (08:30 to 18:00) every day.
Procedure
- Add device areas:
- Click the User tab.
- Select Device User Policy > Authorization Conditions > Device Areas from the navigation tree to open the Device Area List page.
- Click Add to open the page for adding a device area.
- Type the area name and description devArea1 and devArea2.
- Click OK.
- Add an authorized time range policy:
- Click the User tab.
- Select Device User Policy > Authorization Conditions > Time Ranges from the navigation tree to open the Authorized Time Range Policy List page.
- Click Add to open the page for adding authorized time range policy.
- Type the policy name accessTimeWorkingDay.
- Click Add.
The Authorized Time Range Policy Information window appears.
- Select Daily from the Type list, select the start time as 08:30:00 and end time as 18:00:00, and then click OK.
- Click OK.
- Configure a shell profile:
- Click the User tab.
- Select Device User Policy > Authorization Command > Shell Profiles from the navigation tree to open the Shell Profile List page.
- Click Add to open the page for adding a shell profile.
- Type the shell profile name profileLevel and select 2 from the Privilege Level list.
- Click OK.
- Add authorization policies:
- Click the User tab.
- Select Device User Policy > Authorization Policies from the navigation tree to open the Authorization Policy List page.
- Click Add to open the page for adding an authorization policy.
- Type the policy name authorizeAdmin1, and then click Add.
- Select devArea1 from the Device Area list, select Unlimited from the Device Type list, select profileLevel from the Shell Profile list, select Unlimited from the Authorization Command Set list, and then click OK.
- Add a policy named authorizeAdmin2 with the following settings: devArea2 as the device area, unlimited device type, profileLevel as the shell profile, and unlimited authorization command set. (Details not shown.)
- Add a policy named authorizeMaintainer1 with the following settings: devArea2 as the device area, unlimited device type, accessTimeWorkingDay as the authorized time range, profileLevel as the shell profile, and unlimited authorization command set. (Details not shown.)
- Add a policy named authorizeMaintainer2 with the following settings: devArea1 as the device area, unlimited device type, accessTimeWorkingDay as the authorized time range, profileLevel as the shell profile, and unlimited authorization command set. (Details not shown.)
- Click OK.
- Add device users:
- Click the User tab.
- Select Device User > All Device Users from the navigation tree to open the Device User List page.
- Click Add to open the page for adding a device user.
- Add device user names devAdmin1, devAdmin2, devMaintainer1, and devMaintainer2 respectively, select authorizeAdmin1, authorizeAdmin2, authorizeMaintainer1, and authorizeMaintainer2 from the User Authorization Policy list for the device users respectively, and select Enable Privilege-Increase Password for device users devMaintainer1 and devMaintainer2 respectively. (Details not shown.)
- Click OK.
- Device user login through Telnet.
- The following uses the administrator devAdmin1 in the branch devArea1 as an example.
- On the client, select Start > Run, and then type cmd.
- Enter "telnet device IP", and then enter the username and password of the device user devAdmin1.
After the user passes the authentication, the level-2 user privilege level page appears.
- Enter sub and the password to raise the user privilege to the highest level.
- The following uses the maintainer devMaintainer2 in the branch devArea2 as an example.
- On the client, select Start > Run, and then type cmd.
- Enter "telnet device IP", and then enter the username and password of the device user devMaintainer2.
After the user passes the authentication, the level-2 user privilege level page appears. The user privilege cannot be raised and devMaintainer2 can only manage the devices from 08:30 to 18:00 every day.

