User access management networking
The User Access Manager (UAM) Component of the INC provides authentication and authorization for the end users to access the network. The UAM can work with different network access devices such as Ethernet switches, routers, broadband access servers, and VPN access gateways. Developed on the basis of the INC Intelligent Management Platform, the UAM supports centralized management of LAN, WLAN, and VPN access authentication. The UAM can work with other INC components for integrated management of users, resources, and services.
The UAM provides the following service features:
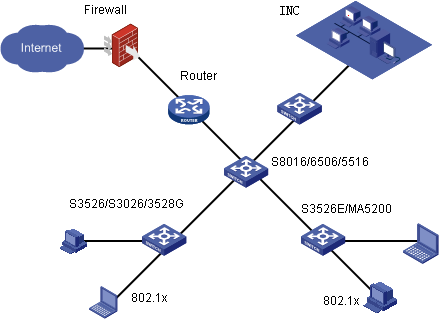
The following figure shows a typical network of the UAM.

User access management networking
The UAM provides three functions: platform user, access user, and user access policy .
User and device are the two fundamental elements of INC and the basis of all network services. User uses the network services. INC provides a centralized user management platform, on which you can apply for a service account for a user to allow it to use of the service.
The user management module provides user grouping, batch import/operation, and supplement information customization functions.
User grouping: You can divide the users into different user groups, specify the operators that can manage each group, and specify the access services available for each group.
Batch user import and operation: You can export user information from other systems, personnel management for example, into files and then import these files into INC, thus reducing your workloads of adding users. This function also reduces your maintenance workloads by modifying the supplement information of or logging out multiple users at a time.
Supplement user information: In addition to user name and contact address, you can also customize supplement attributes for a user, such as department, professional title, and position, for easy user query, maintenance, and grouping. For details, refer to Platform User.
A user of INC can apply for an access service account to get access to the corresponding service. The access user provides access service based user management, including access user query, online user management, binding access users with LDAP server, access details, authentication failure log query, and denylist management.
Online user management: You can query, kick out or add online users to denylist, send them messages, or check the terminals that they use for security. In addition, you can define the columns to be displayed in the all online users, the order in which the columns are to be displayed, and whether sorting is supported.
Binding user with LDAP server: Your network may have LDAP-server-based user information systems (for example, a mail server or a Microsoft Active Directory) currently running. To free the users from memorizing a lot of accounts and passwords, and for easy management and maintenance of user information, INC supports binding access users with the LDAP server for integrated authentication. You can configure the parameters for interaction with the LDAP server in the INC, and bind the access users with the LDAP server, so that the INC will pass the passwords typed by the access users for authentication to the LDAP server for verification.
Access details and authentication failure logs: Each time an access user successfully accesses the network, an access details record is generated, indicating the access start/end time, offline cause, IP/MAC address of the accessing PC, and access device. Each time an access user fails the authentication, an authentication failure log is generated, indicating the failure cause, authentication time, and IP/MAC address of the accessing PC. Access details and authentication failure logs allow you to trace the online behaviors of the access users, and to locate the sources of faults.
Ddenylist: You can add a user to denylist to keep it out of the network temporarily. In addition, a user that fails to type the correct password within certain consecutive tries specified by the threshold is blocked to prevent malicious login attempts. For details, refer to Access User.
User Access Policy provides functions to set the access service parameters, access period policies, access device groups, access services, access devices, and the Portal Server. It also provides access topology management, which allows you to operate the access devices and terminals in the access topology, to monitor and view the access/security status of the access users.
Service parameters: Refer to the global parameters required for the running of the UAM, including level and lifetime of logs, certificate file for certificate authentication, user password strategy that controls the complexity and validity period of passwords, prompt for successful authentication through client, autorun programs/URLs, and user's gateway information against ARP attacks.
Access period policy: You can apply an access period policy to the access users to limit the periods in which the users have access to the network. INC supports fixed access periods and cyclic periods on an annual/monthly/weekly/daily basis. The access period policy is referenced by the access service.
Access device group: An access device group is a collection of access devices, and is referenced by the Do not Bind Access Device Group field. If a service includes both authentication binding information (IP/MAC address or physical port) and unbound access device group setting, users logging in from the devices in the unbound area are free of binding information check. This means they get access to the network despite of binding information incompliance.
Access service: Access service is the core of the UAM. A user must subscribe to an access service before it can use the service. The access service settings for a user specify all the information required for authentication, including authentication mode, binding policy, authorization attributes, and client control policy. A user can subscribe to multiple services with different suffixes. During the authentication, INC matches the domain name following the user name against the suffixes of the services to which the user has subscribed. When a match is found, the corresponding service is applied.
Access device: interacts with the access devices through RADIUS for user authentication and authorization. Therefore, in INC, you need to configure the parameters for interaction with RADIUS, including device IP address, listening port, and shared key. INC can directly call the ACL Management Component to deploy ACLs to the access devices.
Portal Server: INC can act as a Portal Server to interact with the access devices, implementing Portal authentication for access users. To do so, you need to configure the IP address range that supports Portal authentication, access device port for Portal interaction, and the shared key. When necessary, you can also customize the information like Portal authentication page and domain name.
Access topology: Like with the access topology of the network management module, you can add your interested access devices and other closely-related devices to a custom access topology for centralized monitor and management. The access topology provides access device and online user operations such as kicking out a user, sending a message, blocking a user, checking a terminal for security, monitoring the access/security status of a given user or users connected to a given device. For details, refer to User Access Policy.
To take a quick look at user access manager process, refer to User Guide.
For any problems encountered in user access manager , refer to FAQ.