EAD solution networking
The EAD component of INC is the core of the EAD solution. It integrates security policy management, network resources control, and topology monitor.
EAD performs various security checks for terminals in addition to identity authentication and takes action depending on the check result. Depending on your configuration, the action can be Kick Out, Isolate, Inform, or Monitor. The component supports security evaluation, security threat identification, security event awareness and execution of protective measures. It helps avoid network security risks by checking patch control, anti-virus software, anti-spyware software, firewall software, anti-phishing software, hard disk encryption software, ARP attacks, traffic anomalies, vulnerable or illegitimate software, system service startup status, registry errors, share folder vulnerabilities, unregistered assets, and weak operating system passwords. EAD ensures that only secure terminals are connected to the network.
The EAD solution delivers these benefits:
With EAD, you can evaluate the organizational security compliance of a terminal to ensure network security. The evaluation can cover OS patches, third-party software version, anti-virus software version, anti-spyware software version, whether firewall software is running, whether anti-phishing software is installed and applied, whether hard disk encryption software is installed, traffic status of terminal, and some other aspects depending on your configuration.
The terminal used by an online user can trigger security events when, for example, it is infected by viruses. The EAD can isolate these "unhealthy" terminals in real time and allow them to access only the system remediation servers such as the anti-virus, anti-spyware, firewall, anti-phishing, and hard disk encryption software servers and patch servers.
The EAD can deploy the preconfigured control policy to the security client based on the role of the end user, authorizing them access to specific network resources. You can manage and deploy all the security measures such as end user's ACL policy, QoS policy, proxy enabling/disabling and dual-NIC enabling/disabling.
A topology view clearly shows the security information of the access devices in it, such as the numbers of online/insecure users connected to each device. With the topology view, you can monitor the online/security status of a given user or all users connected to a given device. In addition, you can complete management tasks, such as kicking out online users, sending a message, checking computers for security and blocking a user, on the topology view by simple clicks.
For an INC managed device, once it is configured as an access device, you can directly configure ACLs for it with the ACL Manager. This makes it easier to configure device resources for higher efficiency.
The user security statistics to your most concern is shown in an intuitive manner in four charts: 24-Hour Online History, Real-Time Statistical Chart for Online Users, 24-Hour Security History, and Security Chart of the Day.
The security policy server and security proxy can be installed on different servers and configured independently to improve the capacity and performance of the system.
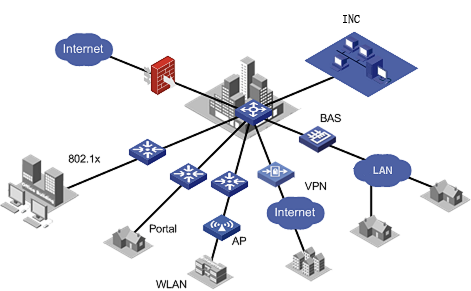
The EAD component is the terminal security policy management platform of the EAD solution. It allows you to perform various terminal/network security checks, and take action depending on check results. This component provides terminal security software control, software control group, patch control, abnormal traffic monitoring, security policy/action management, registry control, share control, asset registration status check, and password control. The following figure shows a typical network with the EAD service enabled.

EAD solution networking
Terminal security software includes anti-virus software, anti-spyware software, firewall software, anti-phishing software, and hard disk encryption software. This function allows you to specify the types of terminal security software that must be installed and run on the terminals, helping protect terminals against attacks and damages after they connect to the network.
This function allows you to specify which software must or must not be installed and which processes must or must not be running and which services must or must not be started up and which files must or must not be existed on the terminals , so as to ensure that only the terminals complying with the security standards get access to the network.
Based on the damages that the Windows security vulnerabilities may cause to the system, you can divide the operating system patches addressing these vulnerabilities into different levels. Based on this division, you can configure the default policy to be applied to the terminals that do not have the required level of hotfix installed. In Linux or Mac OS, the INC EAD checks whether or not the required patching software is installed and normally operates. The patching software, not the INC EAD, checks the system patches.
INC can detect the abnormal traffic originated by online users and take proper measures. This function allows you to set thresholds for IP traffic errors, broadcast packet count errors, severe IP traffic errors, and severe broadcast packet count errors.
The registry monitoring ensures that the terminal PCs with policy-compliant registry are permitted to access the network. The monitor policy can set the registry items to be monitored, and the registry key value.
This function is used to monitoring user local share folders. If INC EAD judge some share folders are not secure, the system can take proper actions (such as alert, isolate, or kick out) based on the policy.
This function works with the INC DAM component to check the registration status of an asset when a user attempts to connect it to the network. If the asset has not been registered, INC kicks the user off, isolates the asset, or asks the user to register the asset as configured.
With the feature enabled, INC EAD can judge whether the operating system password is secure. If not, the system can take proper actions (such as alert, isolate, or kick out) based on the policy.
The security policy and security level management is the core of the EAD. The service subscribed to by a user must include a reference to a certain security policy to be applied. The security policy specifies all aspects concerning the security authentication, such as check items, check mode, remediation policy, online user Real-Time monitor items, and processing policy in case of any check failure. The security level is to be applied to the security policy. A security level specifies the measure, Kick Out, Isolate, Inform, or Monitor, to be taken in case of any check failure. If multiple checks fail, the severest measure is taken.
To take a quick look at the Endpoint Admission Defense process, refer to User Guide.
For any questions encountered in Endpoint Admission Defense, refer to FAQ.
With typical application environments and detailed operation procedures, you can quickly learn the typical applications of Endpoint Admission Defense.